
Synchronized Security
Your Firewall and endpoints are finally talking

UTM Firewall
Simple management:Sophos UTM is easy to use, thanks to the configurable real-time dashboard, flexible modular licensing, and intuitive reusable network object definitions.
Network protection: Easily configure firewall rules that cover multiple destinations, sources, and services. Plus country blocking and intrusion prevention (IPS).
Web protection: Check out the web protection deployment options, policy settings, filter action wizard, policy test tool, and convenient built-in web reports.
App control: Easily control web applications proactively or in real-time using the popular flow-monitor where you can block, shape, or throttle web application traffic on the fly.
Advanced Threat Protection: Advanced Threat Protection (ATP) features include multi-layered protection, selective sandboxing, and the ability to identify infected hosts on your network.
Sophos Access Points
- Simple & Secure Wi-Fi
- Simple Deployment
- Central Management
- Built to Perform
- Increased Visibility
- Hotspots & Guest Access
- Rogue AP Detectionz
- Wireless Scalability
- Site Planning
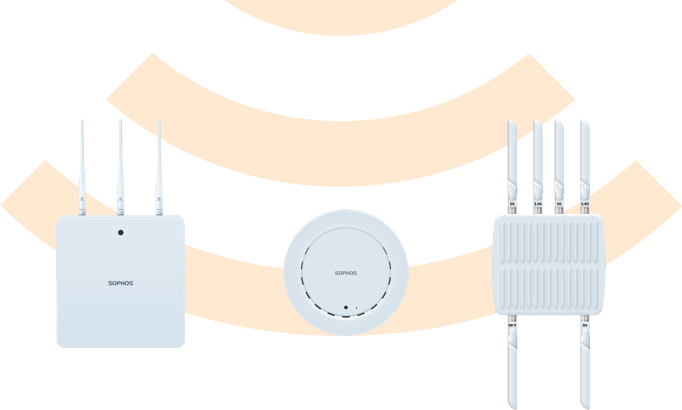
Built to Perform
You get great wireless performance with our range of wireless access points. We have models for indoor and outdoor use, with form factors suiting a range of deployment scenarios and budgets
- Enter-level and enterprise models
- Desktop, wall, and ceiling-mount option
- AP 100X with IP67 rating for exposed environments
Endpoint Protection
- Protect all your devices
- One simplified management console
- On-premise or in the cloud
- Anti Ransomware( Intercept X)
- Next-Gen Protection
- Decloaking Malware
- So Long Malware
- Complete Control
- Sophisticated Simplicity
- Flexible Licensing and Deployment

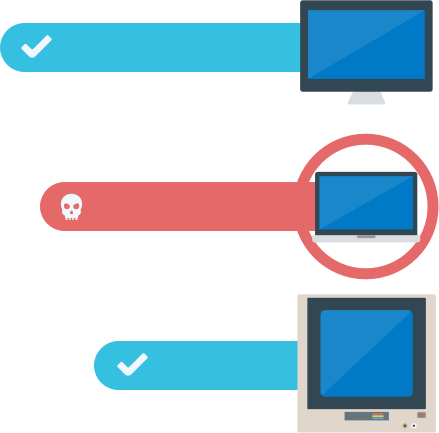
-
Behavioral Analytics
Determines suspicious behaviors, allowing for the detection of malware specifically designed to evade traditional solutions.
-
Traffic Detection
Pre-filters all HTTP traffic and tracks suspicious traffic as well as the file path of the process sending malicious traffic.
-
Integrated Endpoint and Network
Instant and automatic communication between the Endpoint and Network
